Upgrade & Secure Your Future with DevOps, SRE, DevSecOps, MLOps!
We spend hours on Instagram and YouTube and waste money on coffee and fast food, but won’t spend 30 minutes a day learning skills to boost our careers.
Master in DevOps, SRE, DevSecOps & MLOps!
Learn from Guru Rajesh Kumar and double your salary in just one year.
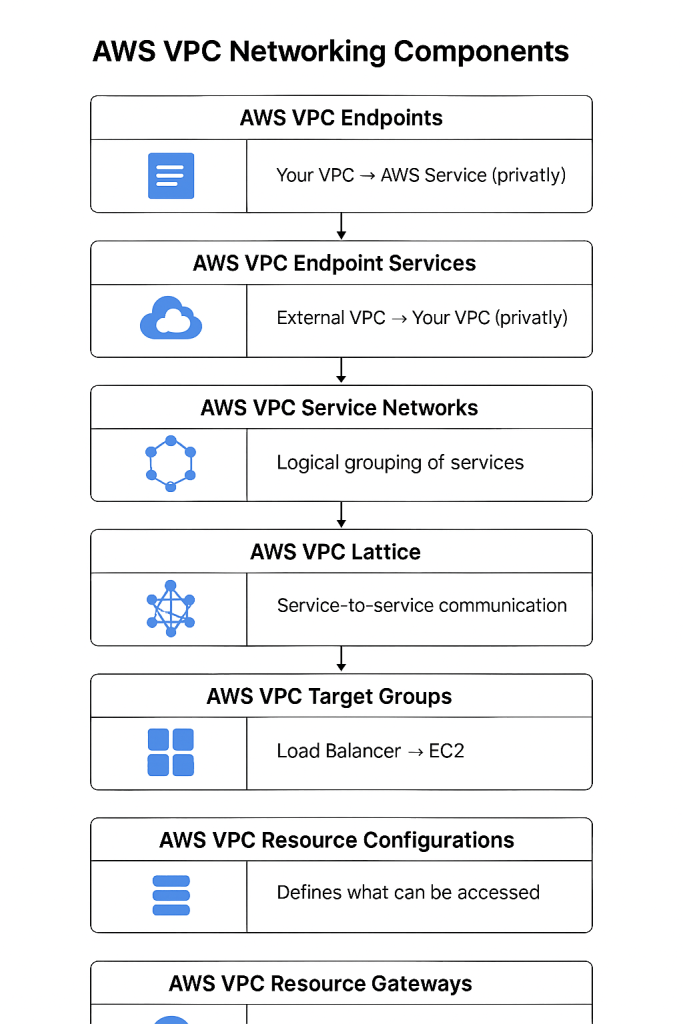
Networking Scope
| Service | Traffic Type | Scope | Direction / Flow |
|---|---|---|---|
| VPC Endpoints | AWS Service Access | Internal VPC | Your VPC → AWS Service (privately) |
| VPC Endpoint Services | PrivateLink Service Sharing | Cross-VPC | External VPC → Your VPC (privately) |
| VPC Service Networks | Microservices Management | Cross-VPC / Multi-account | Logical grouping of services |
| VPC Lattice Services | App-level Service Mesh | Cross-VPC / Multi-account | VPC-A ↔ VPC-B services (via Lattice) |
| VPC Target Groups | Load Balancing Targets | Internal VPC | Load Balancer → EC2/Containers/Lambda |
| Resource Configurations | Shareable Resource Metadata | Your VPC | Defines what can be accessed |
| Resource Gateways | Access Point to Resources | Cross-VPC | External VPCs → Resource in your VPC |
Understanding AWS VPC networking components requires first grasping the fundamental network concepts they’re built upon.
Network Fundamentals
VPC Networks
A Virtual Private Cloud (VPC) is an isolated network environment within AWS that allows you to provision AWS resources in a logically isolated section of the AWS cloud. It’s your private network in the cloud with complete control over:
- IP address ranges
- Subnets
- Routing tables
- Network gateways
AWS Network
The AWS network is the global infrastructure that connects all AWS services and regions. It consists of:
- High-speed fiber connections between regions
- Multiple availability zones within regions
- Edge locations for content delivery
- Private connections that never traverse the public internet
Public Internet Network
The public internet is the global network of interconnected computer networks that use the Internet Protocol (TCP/IP). Unlike AWS’s private network, traffic on the public internet:
- Is visible to anyone who can intercept it
- Takes unpredictable routes
- Has variable performance
- Is susceptible to various security threats
AWS VPC Networking Components
AWS VPC Endpoints
VPC Endpoints allow you to privately connect your VPC to supported AWS services without requiring an internet gateway, NAT device, VPN connection, or AWS Direct Connect.
Practical Example: A company has EC2 instances in a private subnet that need to access an S3 bucket. Without a VPC endpoint, this traffic would need to go through a NAT gateway and over the public internet. With an S3 Gateway endpoint, the traffic stays within the AWS network, improving security and reducing data transfer costs.
AWS VPC Endpoint Services
VPC Endpoint Services (AWS PrivateLink) allow you to expose your own applications as a service to other VPCs, enabling consumers to access your service privately.
Practical Example: A financial services company creates a payment processing API. Instead of exposing this API over the public internet, they create a VPC Endpoint Service. Their customers can then create VPC endpoints in their own VPCs to access the payment API privately and securely.
AWS VPC Service Networks
VPC Service Networks are logical groupings that simplify connectivity across VPCs or accounts and apply common security policies for service-to-service communication.
Practical Example: A large enterprise has dozens of microservices spread across multiple VPCs and AWS accounts. By creating a service network, they can logically group related services together, simplify connectivity, and apply consistent security policies across all services in the network.
AWS VPC Lattice Services
VPC Lattice is a fully managed application networking service that simplifies service-to-service communication with built-in security, observability, and resilience.
Practical Example: A company has a microservices architecture with services running on EC2, ECS, and Lambda across multiple VPCs. With VPC Lattice, they can define a service network, register all their services, and enable secure communication between them with consistent authentication, authorization, and monitoring.
AWS VPC Target Groups
VPC Target Groups are collections of resources (such as EC2 instances) that receive traffic from a load balancer or are part of a VPC Lattice service.
Practical Example: A web application runs on multiple EC2 instances. By creating a target group containing these instances and associating it with a load balancer or VPC Lattice service, traffic can be distributed across all instances, providing scalability and high availability.
AWS VPC Resource Configurations
Resource Configurations define resources or groups of resources within your VPC that you want to make accessible to clients in other VPCs or AWS accounts.
Practical Example: A company wants to share a database cluster with partner organizations. They create a resource configuration specifying the database’s IP address and port range, allowing controlled access to just this specific resource without exposing their entire VPC.
AWS VPC Resource Gateways
Resource Gateways act as entry points into your VPC for accessing the resources defined in your resource configurations.
Practical Example: An organization provides data services to external partners. They create a resource gateway in their VPC and associate it with resource configurations for their databases. When partners access these databases, the traffic enters through the resource gateway, providing a controlled access point.
Use Cases Table
| Component | Use Case 1 | Use Case 2 | Use Case 3 | Use Case 4 | Use Case 5 |
|---|---|---|---|---|---|
| VPC Endpoints | Secure S3 access from private subnets | Private DynamoDB access | Private access to SQS/SNS | Secure API Gateway access | Private ECR image pulls |
| VPC Endpoint Services | Offering private SaaS solutions | Secure partner API access | Multi-tenant service delivery | Cross-account service sharing | Private marketplace offerings |
| VPC Service Networks | Microservices organization | Multi-account service management | Applying consistent security policies | Service discovery across VPCs | Simplified cross-account access |
| VPC Lattice Services | Service mesh implementation | Microservices communication | API gateway functionality | Service discovery and routing | Traffic management between services |
| VPC Target Groups | Load balancing web applications | Container-based service routing | Blue/green deployments | Health-checked service routing | Multi-AZ service distribution |
| VPC Resource Configurations | Database sharing | API endpoint exposure | Legacy system access | Controlled resource sharing | Cross-account resource access |
| VPC Resource Gateways | Secure ingress for shared resources | Multi-account resource access | Partner access to specific resources | Controlled data service access | Hybrid cloud resource sharing |
Interdependencies
Several of these components work together to provide comprehensive networking solutions:
- VPC Endpoints and VPC Endpoint Services: These are complementary – endpoint services are created by service providers, while endpoints are created by consumers to connect to those services.
- VPC Resource Configurations and Resource Gateways: Resource configurations must be associated with a resource gateway, which acts as the entry point for traffic to those resources.
- VPC Service Networks and VPC Lattice Services: VPC Lattice services can be associated with service networks to provide organized service-to-service communication.
- VPC Lattice Services and Target Groups: VPC Lattice services use target groups to define where traffic should be routed.
- VPC Service Networks and Resource Configurations: Resource configurations can be associated with service networks to provide access to resources through the service network.
The most tightly coupled components are:
- Resource Configurations and Resource Gateways (resource configurations require a gateway)
- Endpoint Services and Endpoints (consumers need endpoints to access endpoint services)
- Lattice Services and Target Groups (services need targets to route traffic to)
These components together provide a comprehensive suite of tools for secure, scalable, and manageable networking within and across VPCs in AWS.

 Starting: 1st of Every Month
Starting: 1st of Every Month  +91 8409492687 |
+91 8409492687 |  Contact@DevOpsSchool.com
Contact@DevOpsSchool.com