Upgrade & Secure Your Future with DevOps, SRE, DevSecOps, MLOps!
We spend hours on Instagram and YouTube and waste money on coffee and fast food, but won’t spend 30 minutes a day learning skills to boost our careers.
Master in DevOps, SRE, DevSecOps & MLOps!
Learn from Guru Rajesh Kumar and double your salary in just one year.
To restrict access to a Google Cloud SQL instance so that it is only accessible from selected IP addresses, you can use the Cloud SQL instance’s authorized networks feature. This allows you to specify one or more IP address ranges that are allowed to connect to your database instance. Here’s how you can set this up:
Using Google Cloud Console:
- Navigate to the Cloud SQL Instances page:
- Go to the Google Cloud Console.
- Navigate to the “SQL” section to see a list of your Cloud SQL instances.
- Select the instance you want to configure:
- Click on the instance name to go to its overview page.
- Access the Connections settings:
- Find the “Connections” section in the left-hand menu.
- Click on it to open the connections settings.
- Manage authorized networks:
- In the “Public IP” section, you’ll find the “Authorized networks” setting.
- Click on “Add network” to add a new IP address or range.
- Enter a name for the network and the IP address or range in CIDR notation (e.g.,
192.168.1.0/24for a range or192.168.1.1for a single IP address). - Click “Done” to add the network to the list of authorized networks.
- Save your changes:
- Make sure to click “Save” to apply the changes to your Cloud SQL instance.
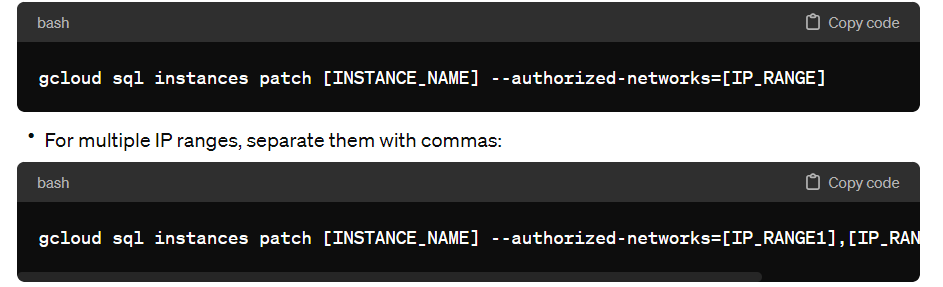
Using gcloud Command Line:
If you prefer using the command line, you can update the authorized networks for your Cloud SQL instance using the gcloud command. Here’s how:
- Set the authorized networks for your instance:
- Use the following command, replacing
[INSTANCE_NAME]with your Cloud SQL instance name, and[IP_RANGE]with the IP address or range you wish to allow in CIDR notation.
- Use the following command, replacing